Wazuh
Wazuh is a free and open source security platform that unifies XDR and SIEM capabilities. It protects workloads across on-premises, virtualized, containerized, and cloud-based environments.
Wazuh helps organizations and individuals to protect their data assets against security threats. It is widely used by thousands of organizations worldwide, from small businesses to large enterprises.
Enabling Docker Listerner in Wazuh
To Enable Docker Listener in Wazuh
To maintain the security and compliance of your Docker environment, it is crucial to proactively monitor both your Docker server and containers. The Docker server is the backbone of your container infrastructure and manages the deployment of containers and resource allocation. By monitoring the Docker server, you can keep track of resource usage, unauthorized access attempts, performance issues, and other security concerns.
However, it is not enough to monitor only the Docker server, you also need to monitor the containers themselves. Container monitoring provides insight into the activities of your containers, such as network connections, file system changes, and process executions. Monitoring these activities helps to detect suspicious behavior, identify malware or malicious processes, and respond to security incidents in real-time.
By monitoring both the Docker server and the containers, you can proactively detect and respond to security threats, ensuring the security and compliance of your Docker environment to regulatory standards.
Wazuh agent configuration
1. Install the dependencies on the docker server :
Run each line Separately
sudo apt-get update && sudo apt-get install python3 -y
sudo apt-get install python3-pip -y
pip3 install docker==4.2.0 urllib3==1.26.182. Edit the File using sudo nano /var/ossec/etc/ossec.conf and add the following:
<!-- Docker Container Runtime configuration -->
<wodle name="docker-listener">
<interval>10m</interval>
<attempts>5</attempts>
<run_on_start>yes</run_on_start>
<disabled>no</disabled>
</wodle>
3. To monitor the logs of the container add the text below to the "<!-- Log analysis -->" section:
<localfile>
<log_format>syslog</log_format>
<location>/var/lib/docker/containers/*/*-json.log</location>
</localfile>4. Restart the wazuh-agent service:
sudo systemctl restart wazuh-agentWazuh server configuration
1. Edit the Decoder File in /var/ossec/etc/decoders/local_decoder.xml on the Wazuh Server and add:
<decoder name="web-accesslog-docker">
<parent>json</parent>
<type>web-log</type>
<use_own_name>true</use_own_name>
<prematch offset="after_parent">^log":"\S+ \S+ \S+ \.*[\S+ \S\d+] \.*"\w+ \S+ HTTP\S+" \d+</prematch>
<regex offset="after_parent">^log":"(\S+) \S+ \S+ \.*[\S+ \S\d+] \.*"(\w+) (\S+) HTTP\S+" (\d+)</regex>
<order>srcip,protocol,url,id</order>
</decoder>
<decoder name="json">
<parent>json</parent>
<use_own_name>true</use_own_name>
<plugin_decoder>JSON_Decoder</plugin_decoder>
</decoder>2.Restart the Wazuh-Manager:
sudo systemctl restart wazuh-managerWazuh Docker listener dashboard
The Wazuh Docker listener dashboard offers a centralized and user-friendly interface that allows you to monitor the security of your Dockerized infrastructure. With real-time insights and actionable information, the Wazuh Docker listener dashboard empowers system administrators and security teams to detect and respond to potential threats, ensuring the integrity and reliability of containerized applications. From monitoring container events to analyzing logs and implementing custom rules, this dashboard streamlines the security management process, enhancing the overall protection of your Docker environment.
Take the following steps to enable the Wazuh Docker listener dashboard:
-
Click on the Wazuh menu icon, and select Settings > Modules.
-
Scroll down to the Threat Detection and Response section and enable Docker listener.
-
Click on the Wazuh menu icon, and select Modules > Docker listener to view the Docker listener dashboard.
The animation below is a graphical representation of the steps you need to take to enable the Wazuh Docker listener dashboard.
Wazuh Docker listener configuration options
In this section, we provide more information about the Wazuh Docker listener and all possible configuration options. The Docker listener has the main options and the scheduling options.
Main options
The main options allow you to enable or disable the Docker listener, and to configure the number of attempts to rerun the listener in case it fails. The two main options are disabled and attempts.
disabled
The disabled option allows you to enable or disable the Docker listener.
|
Default value |
no |
|
Allowed values |
yes, no |
attempts
The attempts option specifies the number of attempts to execute the listener in case it fails.
|
Default value |
5 |
|
Allowed values |
A positive number |
Scheduling options
The scheduling options allow you to configure when the Docker listener should execute. The available scheduling options are run_on_start, interval, day, wday, and time. The Docker listener runs on start by default when enabled without any scheduling options.
run_on_start
Run the Docker listener immediately when the Wazuh agent starts.
|
Default value |
yes |
|
Allowed values |
yes, no |
interval
Waiting time to rerun the Docker listener in case it fails.
|
Default value |
1m |
|
Allowed values |
A positive number that should contain a suffix character indicating a time unit, such as s (seconds), m (minutes), h (hours), d (days), M (months). |
day
Day of the month to run the scan.
|
Default value |
n/a |
|
Allowed values |
Day of the month [1..31] |
Note
When the day option is set, the interval value must be a multiple of months. By default, the interval is set to a month.
wday
Day of the week to run the scan. This option is not compatible with the day option.
|
Default value |
n/a |
|
Allowed values |
Day of the week:
|
Note
When the wday option is set, the interval value must be a multiple of weeks. By default, the interval is set to a week.
time
Time of the day to run the scan. It has to be represented in the format hh:mm.
|
Default value |
n/a |
|
Allowed values |
Time of day [hh:mm] |
Note
When only the time option is set, the interval value must be a multiple of days or weeks. By default, the interval is set to a day.
Example configuration
The example configuration below shows an enabled Docker listener. The listener attempts to execute five times at ten-minute intervals if it fails
<wodle name="docker-listener"> <interval>10m</interval> <attempts>5</attempts> <run_on_start>no</run_on_start> <disabled>no</disabled> </wodle>
Docker container security monitoring with Wazuh
Docker has become a popular framework for application deployment since its development due to its benefits. For example, it makes it easier for organizations to enhance the portability of their applications and operational resilience. Docker is an open source technology used to package applications into containers. Docker containers are lightweight, standalone, and runnable instances of a Docker image that isolate software running in the container from the operating system environment. With these benefits, many organizations have adopted the technology to quickly package their software in standard units for development, shipment, and deployment.
The increased usage of containerized software has increased the attack surface for organizations. This provides an additional asset for cyber threat actors to target in their attacks. Therefore, it is crucial to continuously monitor containers to gain complete visibility of their environment and events during execution.
In this blog post, we demonstrate how to do the following:
- Monitor Docker events such as
pull,create,start,mount,connect,exec_start,detach,die,exec_create,exec_detach, etc. - Monitor Docker container resources such as CPU, memory, and network traffic utilization.
- Detect when container CPU and memory usage exceed predefined thresholds.
- Monitor the health status and uptime of Docker containers.
Docker Container: Infrastructure setup
The following setup is used to illustrate the capability of Wazuh to monitor Docker container events and their metrics:
- A Centos 7 endpoint running the Wazuh 4.3.10. The Wazuh central components can be installed using this Quickstart installation guide.
- An Ubuntu 22.04 endpoint running the Wazuh agent 4.3.10. This endpoint also hosts the Docker container infrastructure. This Wazuh guide is used to install the Wazuh agent.
Monitoring with Wazuh
Wazuh has the Docker listener and command monitoring modules that can be used to collect security and runtime events from Docker containers. The Docker listener module communicates with the Docker API to collect events related to Docker containers. The command monitoring module is used to monitor the output of specific commands and trigger alerts if they match a rule.
Ubuntu endpoint configuration
Follow these steps on the monitored endpoint:
Note
You need root user privileges to execute all the commands described below.
1. Install Python and pip:
2. Install Docker and the Python Docker Library to run the containers:
3. Enable the Wazuh agent to receive remote commands from the Wazuh server. By default, remote commands are disabled in agents for security reasons.
4. Restart the Wazuh agent to apply the above changes:
Wazuh server configuration
Follow these steps on the Wazuh server:
Note
You need root user privileges to execute all the commands described below.
1. Create a Wazuh agent group called container:
2. Obtain the ID of all Wazuh agents using the following command:
3. Assign the Wazuh agent hosting the Docker containers to the container group. Multiple agents can be assigned to the group. This ensures all agents running Docker containers in your environment receive the same configuration.
Replace <AGENT_ID> with the agent’s ID of the endpoint hosting the Docker container.
4. Add the following settings to the /var/ossec/etc/shared/container/agent.conf configuration file. This enables the Docker listener module and sets the commands to execute on the monitored endpoint for Docker container information gathering.
Note
The <frequency> tag defines how often the command will be run in seconds. You can configure a value that suits your environment.
The commands to extract information configured above can get logs like in the following samples:
- Log for container resources:
- Log for container health:
5. Create a decoders file docker_decoders.xml in the /var/ossec/etc/decoders/ directory and add the following decoders to decode the logs received from the Wazuh agent:
Note
The custom decoder file docker_decoders.xml might be removed during an upgrade. Ensure to back up the file before you perform upgrades.
6. Create a rules file docker_rules.xml in the /var/ossec/etc/rules/ directory and add the following rules to alert the container information:
Note
The custom rules file docker_rules.xml might be removed during an upgrade. Ensure to back up the file before you perform upgrades.
7. Restart the Wazuh manager to apply the above changes:
Testing the configuration
To showcase the use cases mentioned above, Nginx, Redis, and Postgres images are used to create a containerized environment on the monitored endpoint.
1. Create and switch into a project directory /container_env for the container environment using the following command:
2. Create a Docker compose file docker-compose.yml and add the following configurations to it. The Docker compose file helps to manage multiple containers at once. The configuration performs the following Docker actions:
- Pulls Nginx, Redis, and Postgres container images from Docker Hub.
- Creates and starts
nginx-container,redis-container, andpostgres-containercontainers from the respective Docker images. - Creates and connects to a network called
container_env_network. - Creates and mounts volumes
container_env_dbandcontainer_env_cache. - Performs health checks on the created containers every three minutes.
3. Execute the following command in the path containing the docker-compose.yml file to create and start the containers:
4. we use the stress-ng utility program to test for high CPU and memory utilization. Perform this test on one of the containers, for instance, the nginx-container.
- Execute the following commands to enter the container shell and install the stress-ng utility:
- Execute the following command to trigger a high-level alert when both CPU and memory utilization exceeds 80%. The command runs for 3 minutes.
- Execute the following command to trigger a high-level alert when memory usage exceeds 80%. The command runs for 3 minutes.
- Execute the following command to trigger a high-level alert when CPU usage exceeds 80%. The command runs for 3 minutes.
5. The health check for the nginx-container verifies whether the configuration file /etc/nginx/nginx.conf exists. While inside the container shell, delete the configuration file to trigger a high-level alert when the container becomes unhealthy:
Alert visualization
Visualize the triggered alerts by visiting the Wazuh dashboard.
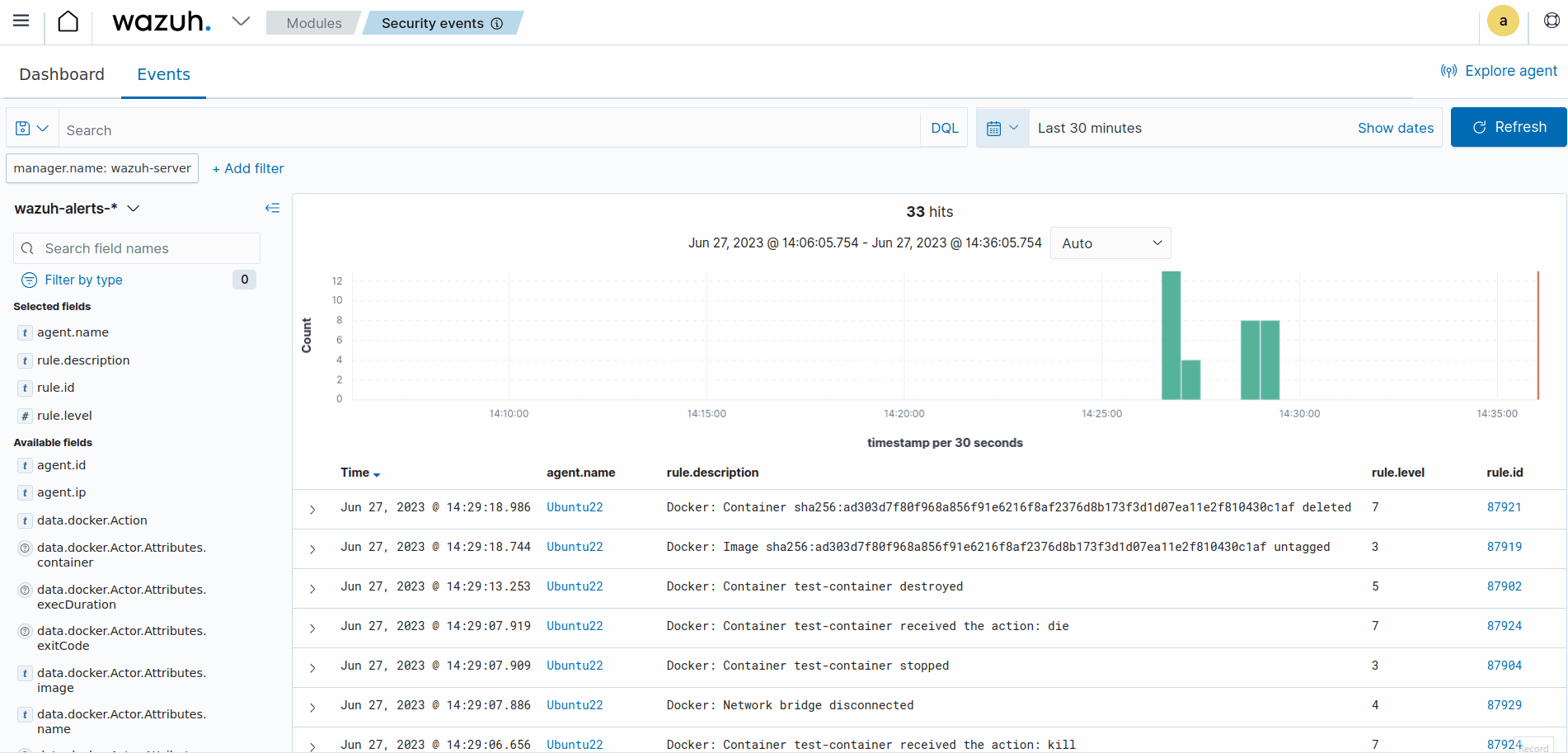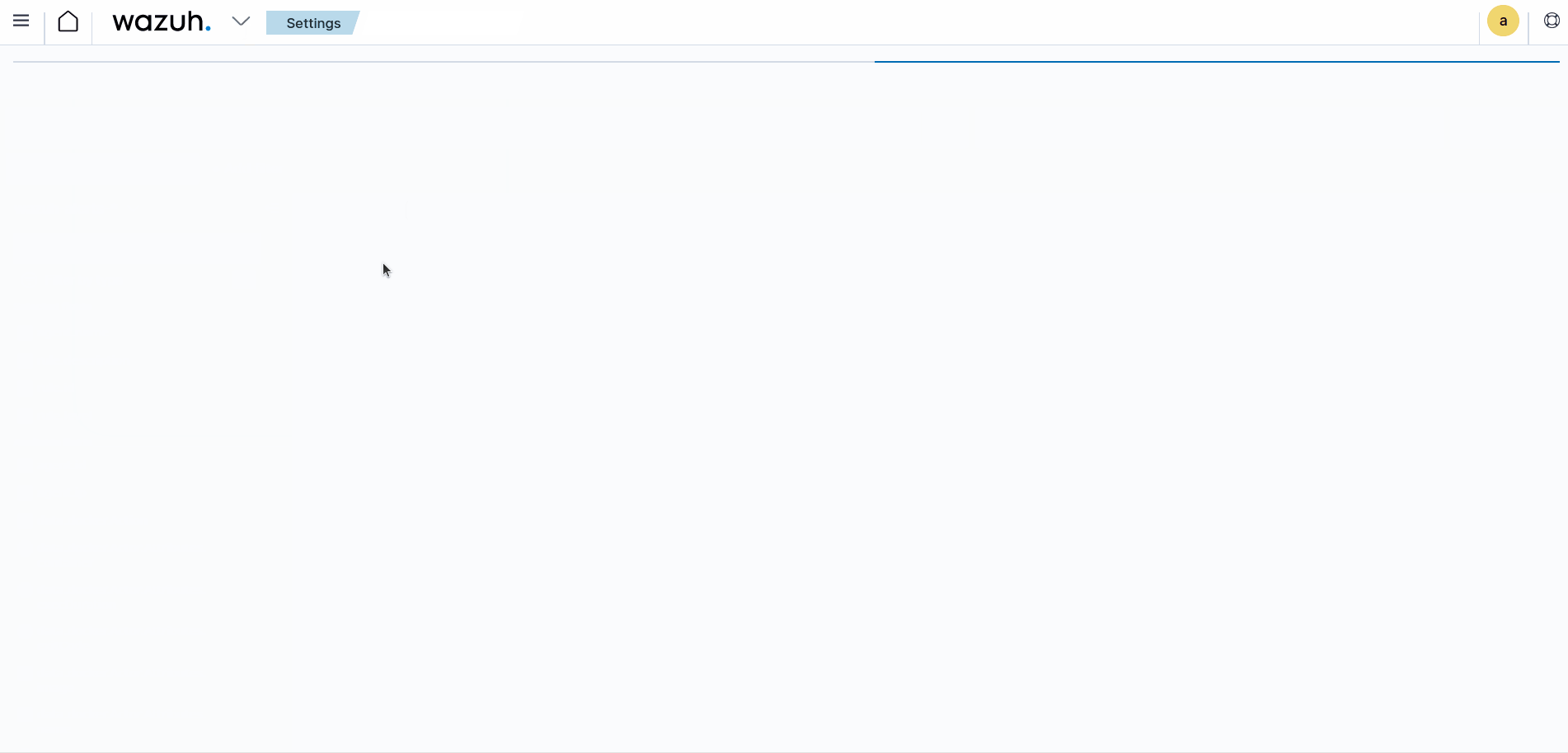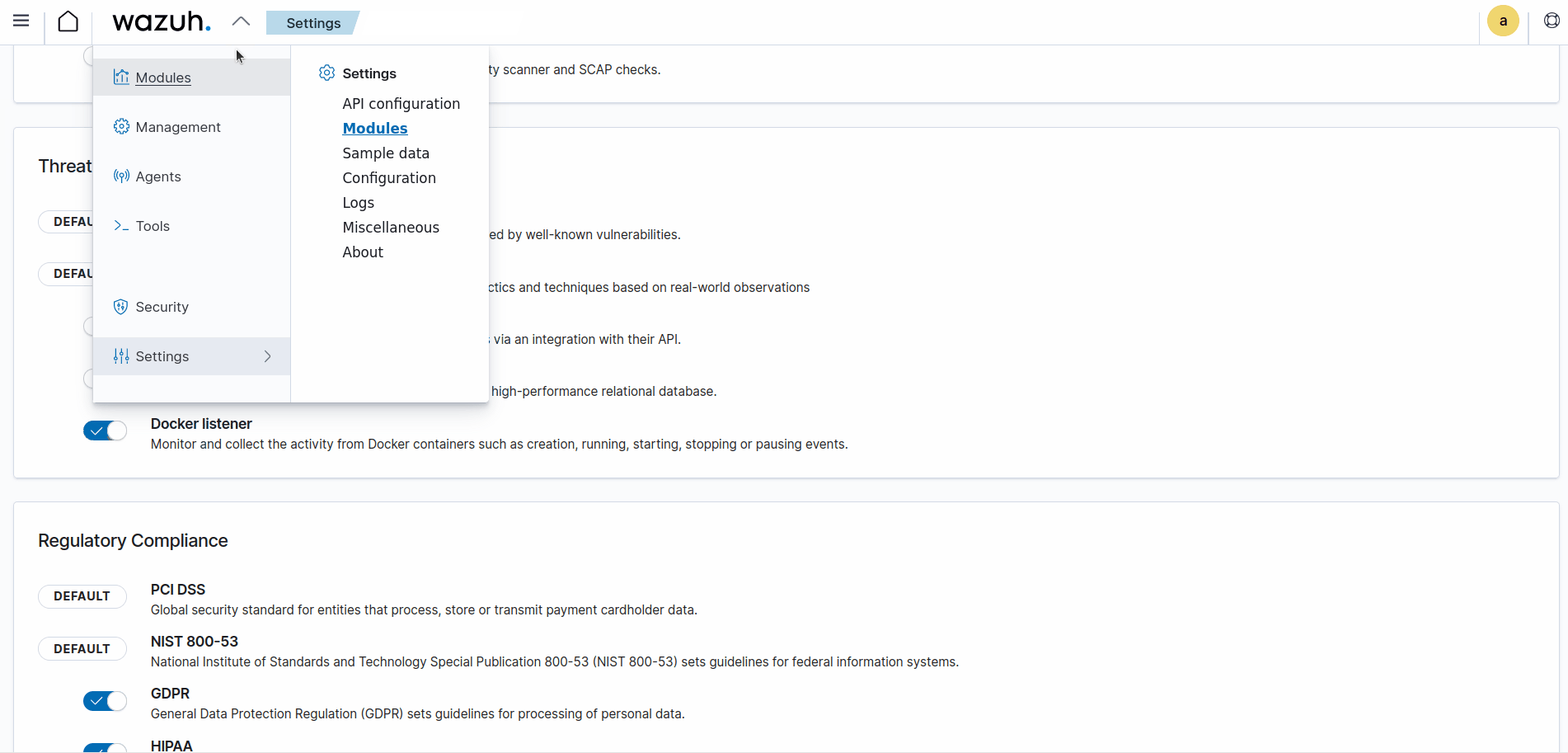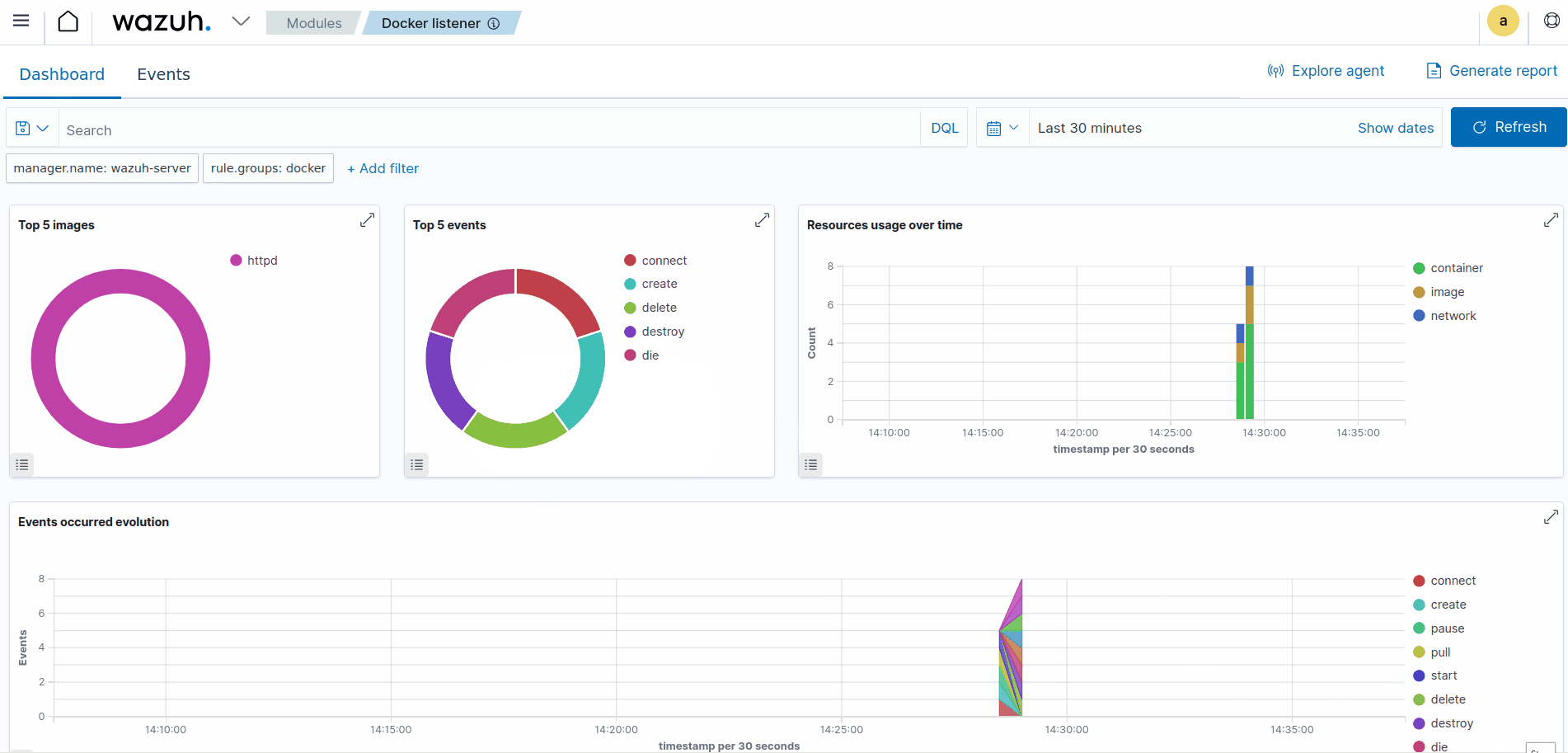
- Container actions alerts: Navigate to the Discover section and add the
rule.groups: dockerfilter in the search bar to query the alerts. Also, use the Filter by type search field and apply theagent.name,data.docker.from,data.docker.Actor.Attributes.name,data.docker.Type,data.docker.Action, andrule.description, filters. Save the query as Docker Events.

- Container resources alerts: Navigate to the Discover section and add the
rule.id: (100100 OR 100101 OR 100102 OR 100103)filter in the search bar to query the alerts. Also, use the Filter by type search field and apply theagent.name,data.container_name,data.container_cpu_usage,data.container_memory_usage,data.container_memory_limit,data.container_network_rx, anddata.container_network_txfilters. Save the query as Container Resources.

- Container health alerts: Navigate to the Discover section and add the
rule.id: (100105 OR 100106)filter in the search bar to query the alerts. Also, use the Filter by type search field and apply theagent.name,data.container_image,data.container_name,data.container_health_status, anddata.container_uptimefilters to show the status information. Save the query as Container Health.

- Container threshold events: Navigate to the Wazuh > Security events section and add the
rule.id: (100101 OR 100102 OR 100103 OR 100106)filter in the search bar to query the alerts.

To have a single display of the visualizations, create a custom dashboard with the above templates. Navigate to OpenSearch Dashboards > Dashboard > Create New Dashboard, then select Add an existing link and click the saved visualizations (Docker Events, Container Resources, and Container Health). This will add the visualizations to the new dashboard. Save the dashboard as Container-resource-health-events.

Conclusion
High visibility of containers in Dockerized environments allows you to maintain a secure and efficient environment. This way, organizations can quickly identify and respond to issues and minimize disruptions. With Wazuh, we can spot abnormalities in containers, get an overview of their resource utilization, and easily analyze their health.
In this blog post, we ensured complete coverage of our Dockerized environment by monitoring Docker container events, resource utilization, and health to improve overall security.